Overview
JS AUDITOR is a comprehensive JavaScript auditing tool that performs deep analysis of JavaScript files. It scans for exposed URLs, endpoints, query parameters, and potential secrets, while also detecting JavaScript Sourcemap files. This multi-faceted approach helps identify information disclosure risks (CWE-200) and other potential security issues within JavaScript code, enhancing overall application security.Usage Examples
You can specify a list of target URLs for JSAUDITOR to check for common vulnerabilities found in JavaScript files. Optionally, you may configure any settings you’d like. Afterward, simply click on Scan to launch your scan. Shortly after your scan has been launched, you will be redirected to the page to view your pending scan.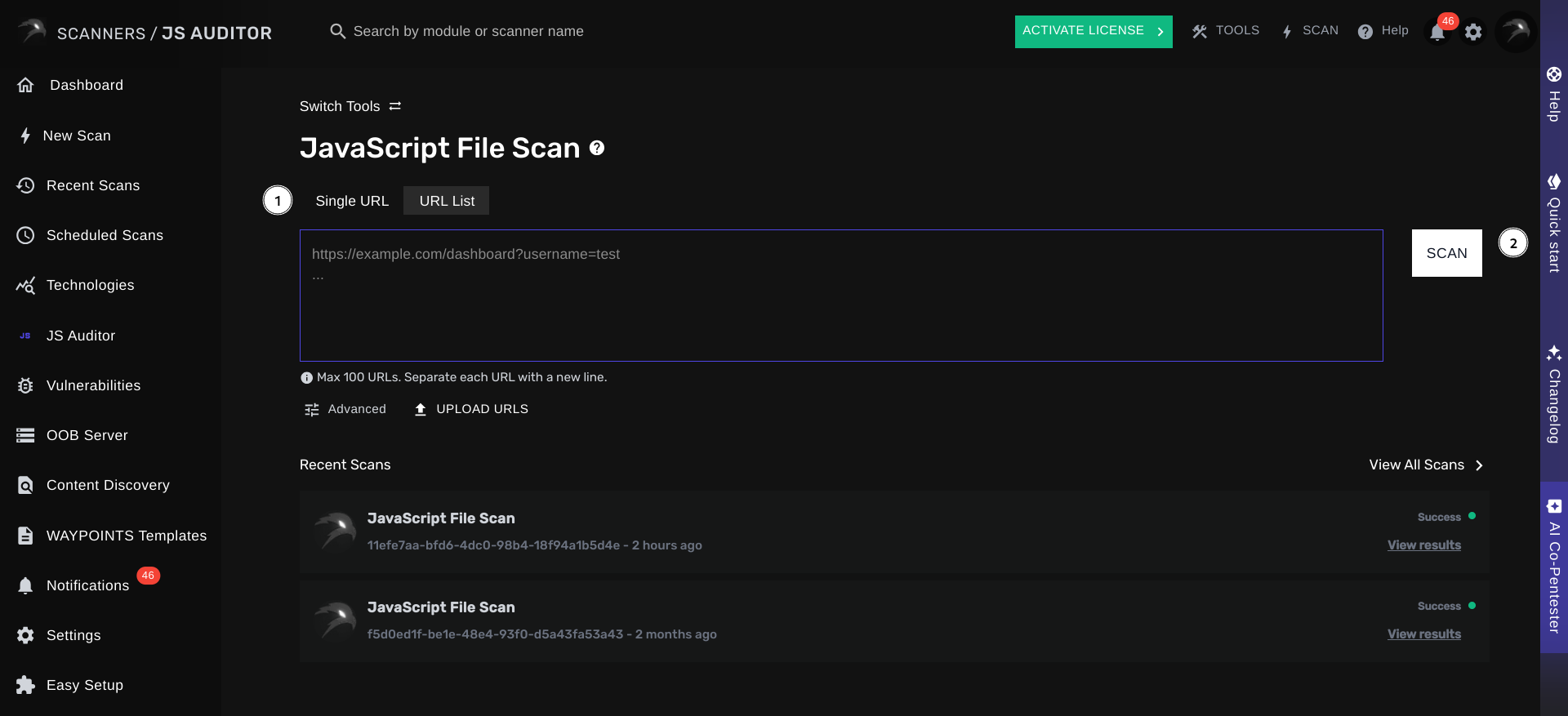
Capabilities
JSAUDITOR is a comprehensive JavaScript auditing tool equipped with the following capabilities:70+ Fingerprints For Hard-Coded Secrets
70+ Fingerprints For Hard-Coded Secrets
JSAUDITOR is equipped with over 70 fingerprints to detect hard-coded secrets, tokens and API keys.
Link & Input Parameter Discovery
Link & Input Parameter Discovery
JSAUDITOR is capable of reporting back links and any referenced input parameters. References and links in JavaScript code to files, API endpoints and application routes are always worth examining.
Dependency Confusion Detection
Dependency Confusion Detection
JSAUDITOR is capable of finding and examining NodeJS build configuration files (such as
package.json and package-lock.json) to enumerate NPM packages and check their availability.JavaScript Sourcemap Detection
JavaScript Sourcemap Detection
JSAUDITOR is capable of discovering and unpacking JavaScript Sourcemap files in an attempt to discover more references to links, URLs, API endpoints and input parameters.
Lightweight
Lightweight
JSAUDITOR is lightweight by default and is capable of scanning your JavaScript file in mere seconds.