Private OAST Server
OAST Server
OAST Server is your personal private Out-of-Band (OOB) Server designed for Out-of-band Application Security Testing (OAST).
What is your OAST Server?
OOB Server is your personal private Out-of-Band (OOB) Server designed for Out-of-band Application Security Testing (OAST). This dedicated infrastructure allows security professionals to detect and validate vulnerabilities that rely on external service interactions, such as Blind SQL Injection, Blind Cross-Site Scripting (XSS), Server-Side Request Forgery (SSRF), and XML External Entity (XXE) attacks.Setting up your OAST Server
To start making use of your OAST server, you’d have to select your canary token name first. This is an identifier that will help us forward any requests to you to make them visible in your account. The setup process is straightforward:1
Initial Setup
Sign in to your account and navigate to /oast-server/setup
2
Select a Canary Token Name
Choose a unique identifier for your OOB server. This will be your subdomain in the format:
{name}.x7.rs.3
Listen for Interactions
That’s it, you’ll now be redirected to the page where you can view your live DNS, HTTP and Blind XSS interactions.
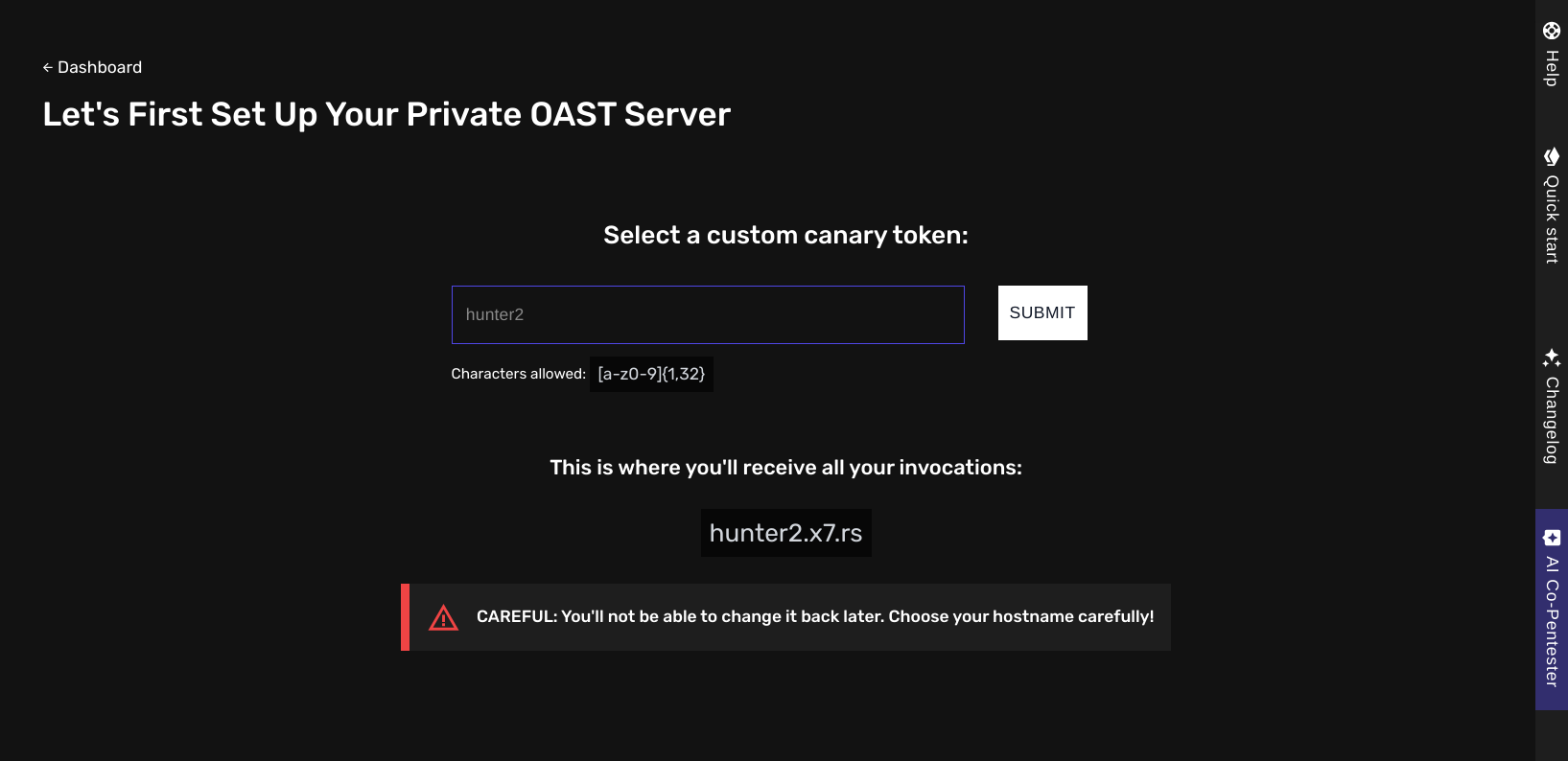
A canary token must be between 1 and 32 characters in length and can only contain lowercase letters (a-z), numbers (0-9).
Your canary token cannot be changed after initial setup for security and privacy reasons. Please select your canary token carefully.
Blind XSS Server
Your private OAST server is also capable of helping you with detecting blind cross-site scripting vulnerabilities. Here’s an example of a blind XSS payload that makes use of your unique canary token:BLACKBIRD’s native Cross-Site Scripting (XSS) scanner is also capable of injecting your blind XSS payloads with a unique random ID! Later, when your blind XSS triggers, you will be able to easily trace back the scan that caused the blind XSS to be triggered.
Payloads
Your OAST server is also equipped with several payloads for Cross-Site Scripting, Remote File Inclusion (RFI), etc.SVG payload
Requesting any of the following paths on your canary token will return the SVG payload:/s/v/g
Example:
https://demo.x7.rs/s will return an SVG payload. This enables us to use XSS payloads with the SVG element for example.RFI payload (PHP)
Requesting the following path on your canary token will return the Remote File Inclusion payload for PHP:/include_me.php
This payload is also used by your LFI, RFI and LFD scanner.
Redirects
Redirects are also supported. On some occasions, you’d need to initiate an arbitrary redirect for out-of-band vulnerabilities. The following endpoint allows you to initiate a server-side redirect to an arbitrary host:/r?u=https://example.com
Notifications
If you have set up notifications on your account, you will receive alerts for new Blind XSS vulnerabilities.Supported Invocation Types
At the moment, your OOB server supports 3 different- DNS
- HTTP
- HTTPS
Support for SMTP, FTP and other protocols will be added over time.
