Overview
S9R (SSRFSCANNER) is a specialized tool designed to detect both full and blind Server-Side Request Forgery (SSRF) vulnerabilities. SSRF (CWE-918) is often considered a high-severity issue due to its potential to bypass security controls, access internal resources, or perform unauthorized actions on behalf of the server. S9R’s comprehensive approach helps identify these critical security flaws effectively.Usage Examples
You can specify a list of target URLs for S9R to check for Server-Side Request Forgery vulnerabilities. Optionally, you may configure any settings you’d like. Afterward, simply click on Scan to launch your scan. Shortly after your scan has been launched, you will be redirected to the page to view your pending scan.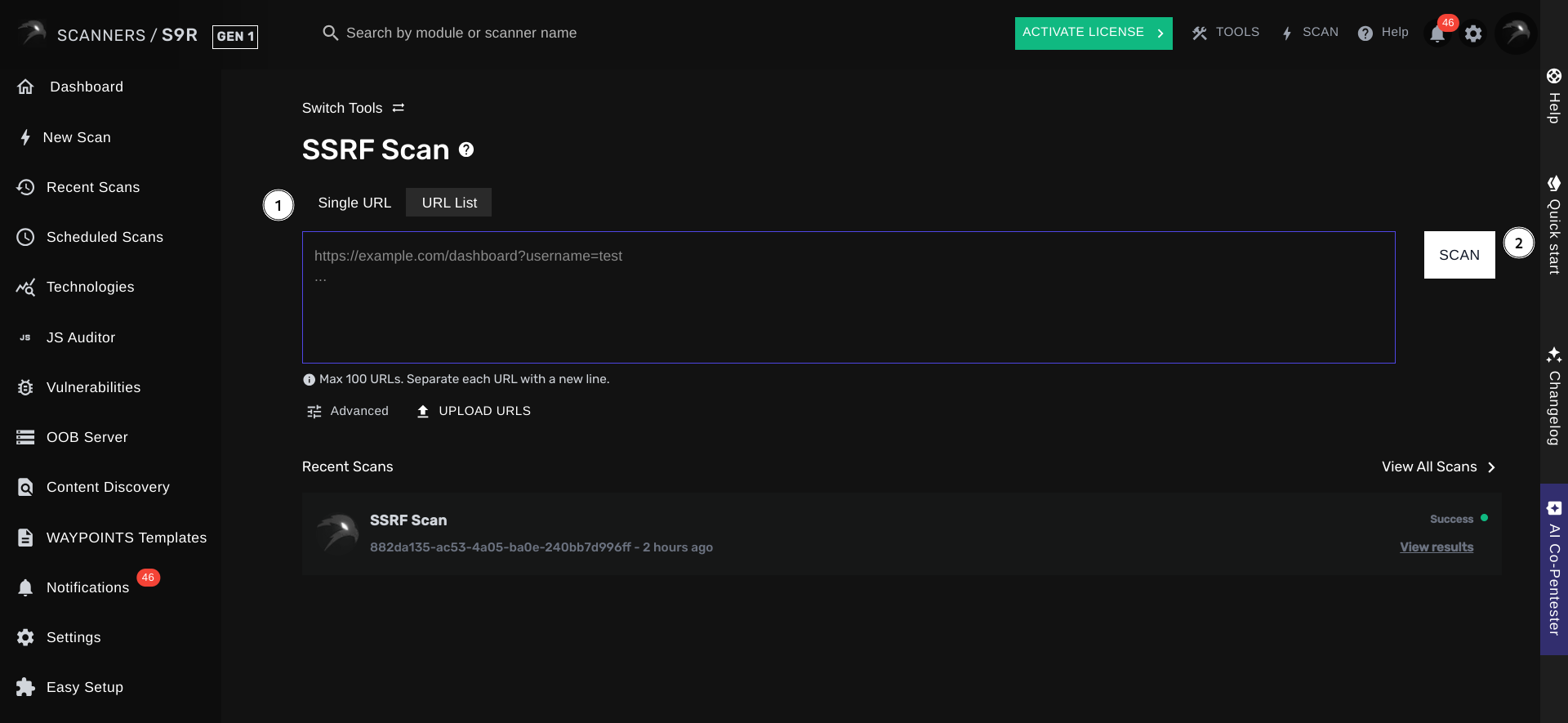
Capabilities
S9R is an advanced Server-Side Request Forgery (SSRF) scanner equipped with the following capabilities:Server-Side Request Forgery (SSRF) Detection
Server-Side Request Forgery (SSRF) Detection
S9R is an advanced tool to help you detect Full and Blind Server-Side Request Forgery (SSRF) vulnerabilities.
Integrated OAST Server
Integrated OAST Server
S9R uses your private OAST Server to validate flagged vulnerabilities to provide a false-positive free experience.
Advanced Payloads With WAF Bypasses
Advanced Payloads With WAF Bypasses
Advanced Payloads with Web Application Firewall (WAF) bypasses for popular firewalls like Cloudflare, Akamai, etc.